Looking Good Info About How To Stop Smurf Attack
Summary a smurf attack is a type of ddos attack that takes advantage of vulnerabilities in ip and icmp protocols to render a network inoperable.
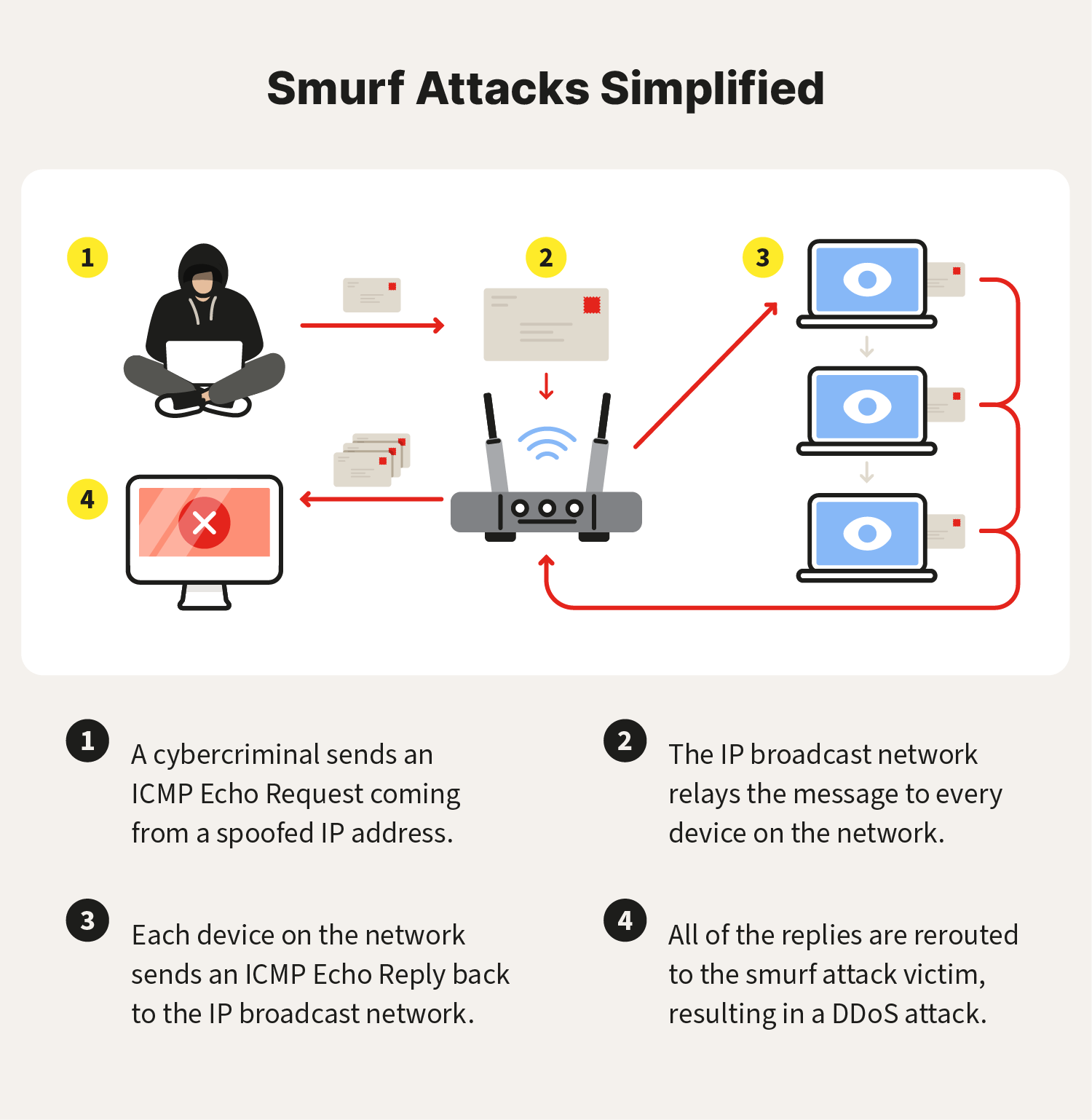
How to stop smurf attack. The packet contains an icmp ping message, which commands network nodes to send a reply. What is the difference between a smurf attack and a fraggle attack? How to prevent a smurf attack?
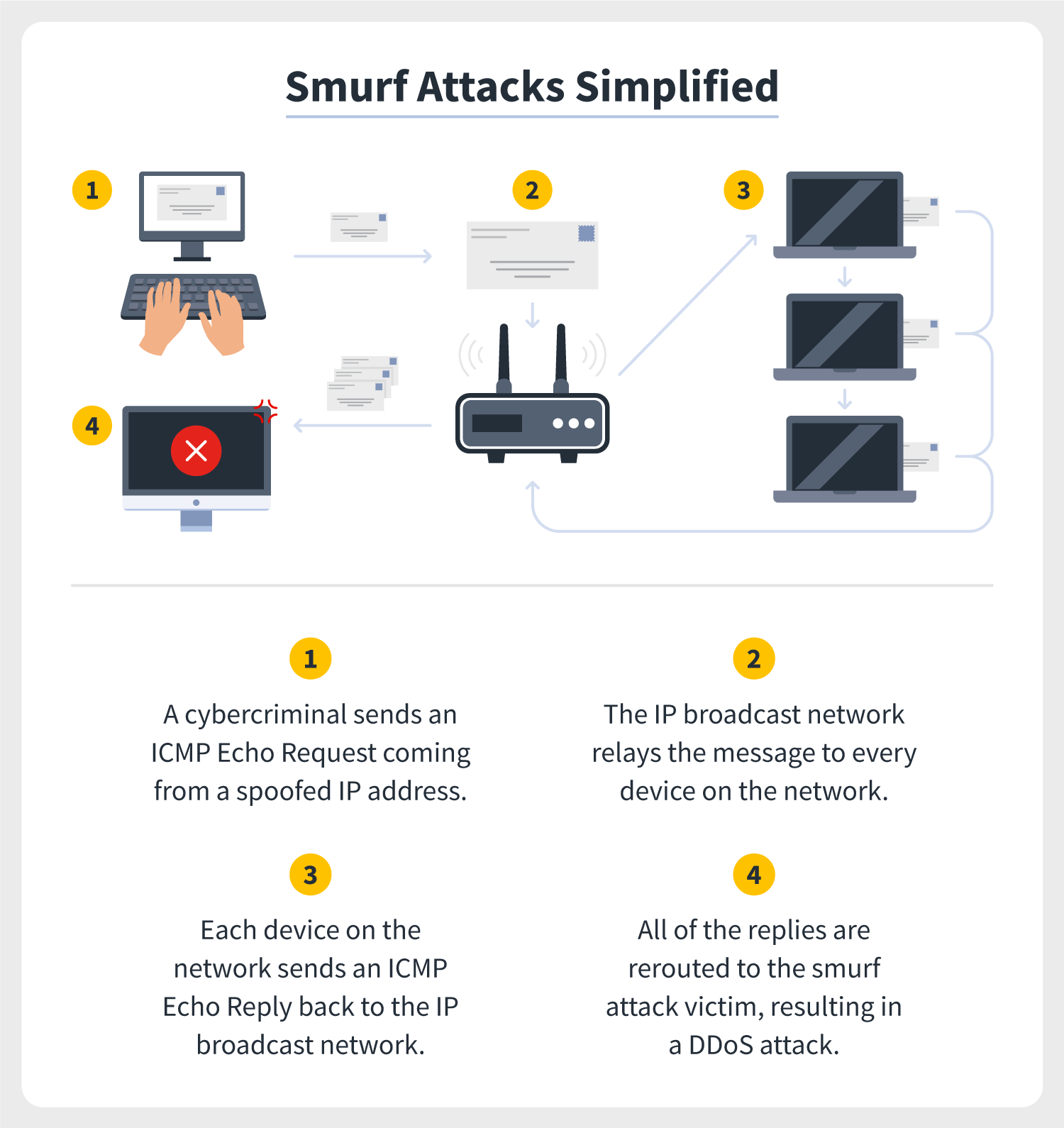
Our guide to enhancing cybersecuritywill help you understand general malware prevention techniques and good digital hygiene. It should not be confused with the amiable blue animated characters. How a smurf ddos attack works.
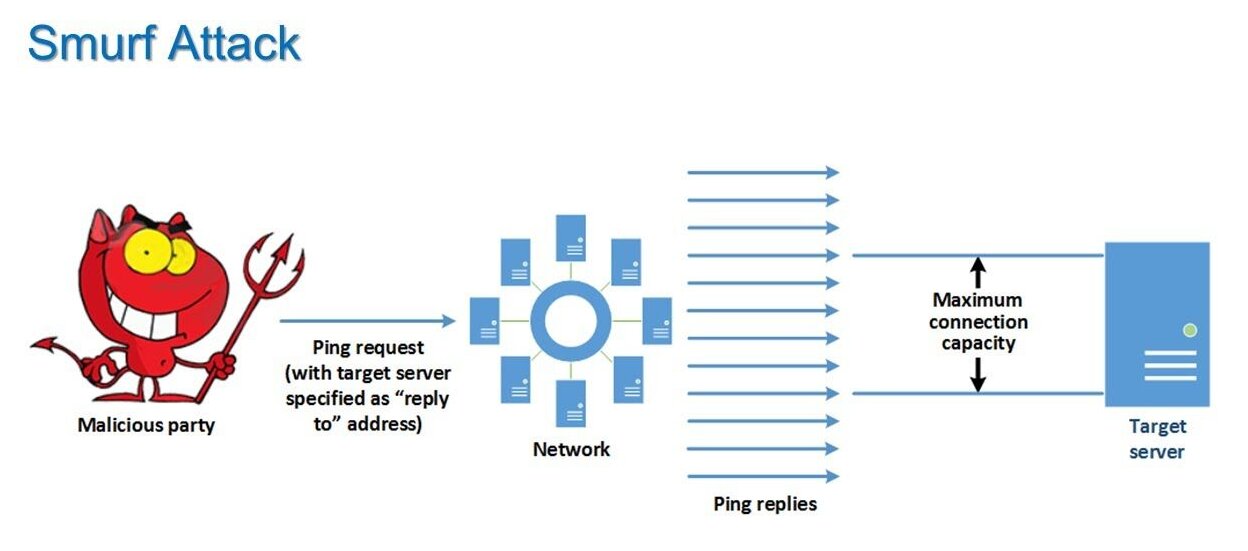
A smurf attack uses crafted internet control message protocol (icmp) echo request packets to overwhelm a targeted device. Interested viewers may find the following links useful:what is the smurf attack and how t. The term (smurf) was first introduced in the late 1990s.
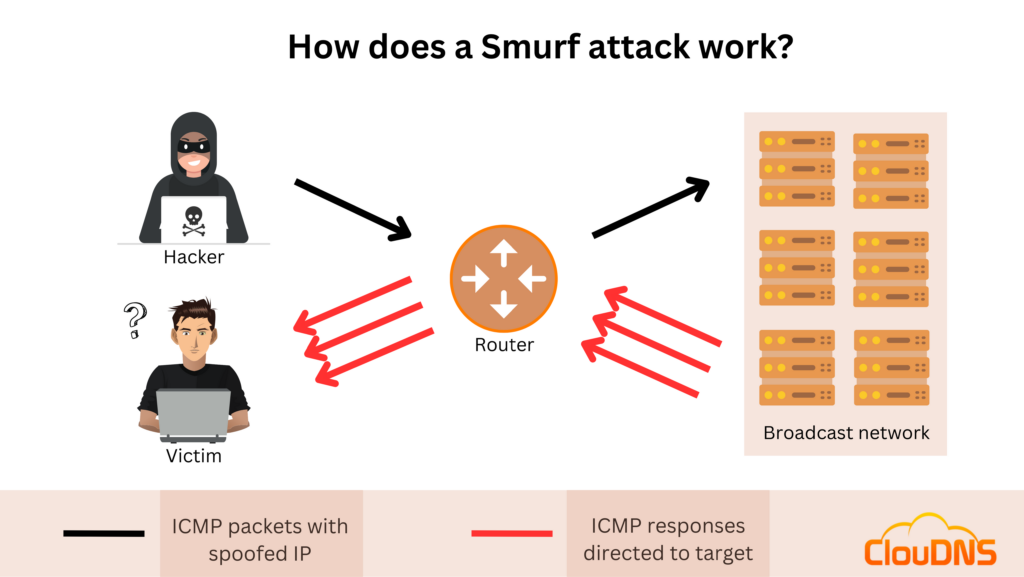
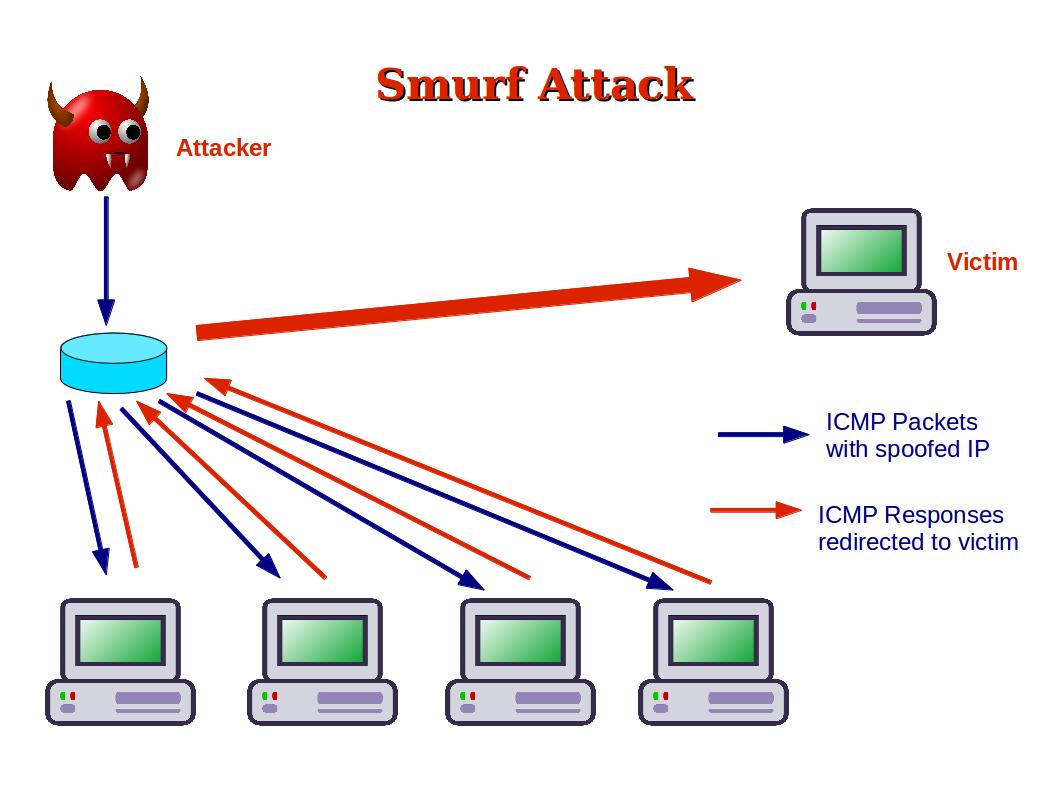
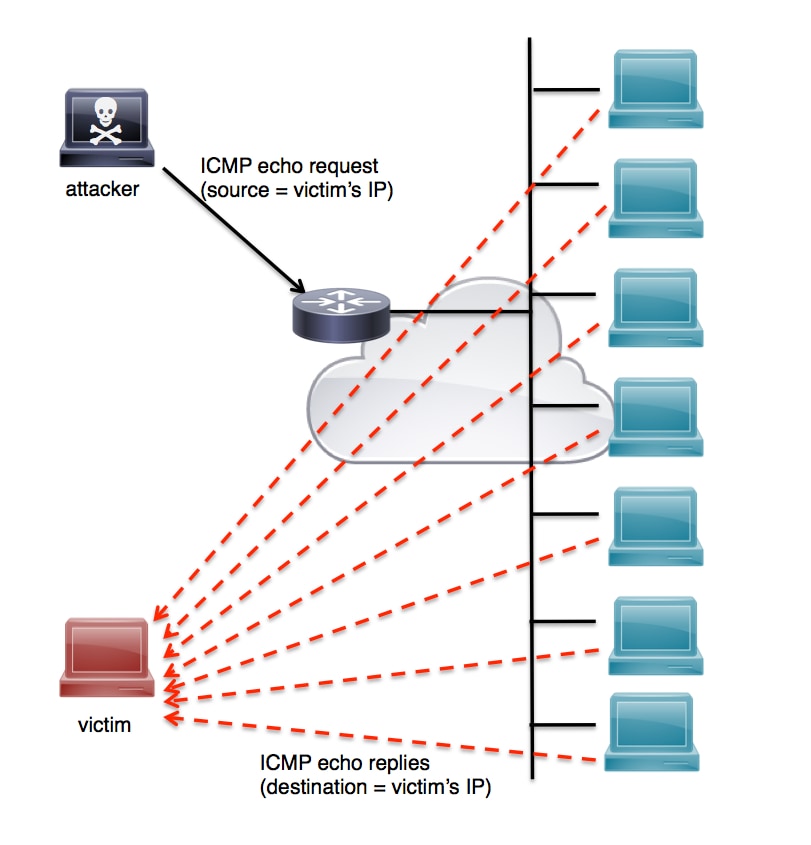
A smurf attack is a kind of dos attack where an attacker causes a victim to be flooded with icmp echo (pping) replies sent from another network. This video explains what the smurf attack is and how to prevent it. Smurf attacks have been used by hackers for many years and continue to pose a significant threat to organizations around the world.
Definition & defense | okta identity 101 what is a smurf attack? 18 december 2023 safeaeon inc. Smurf amplifiers act to worsen the severity of a smurf attack because they are.
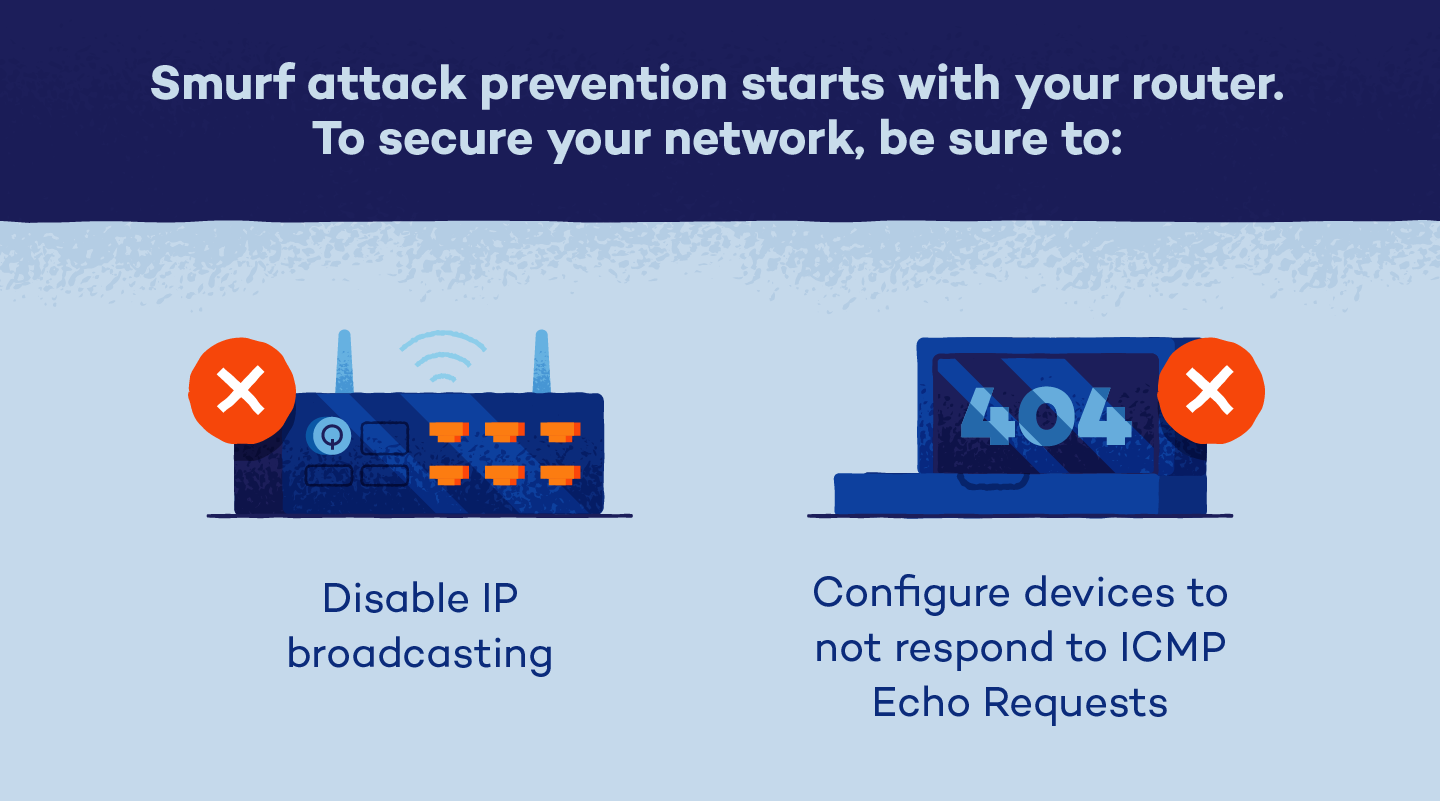
Haseeb awan april 5, 2023 cyber security smurf attacks are a common type of cyber attack that can wreak havoc on computer networks and systems. Here are a couple of steps to for smurf attack mitigation: How to prevent smurf attack?
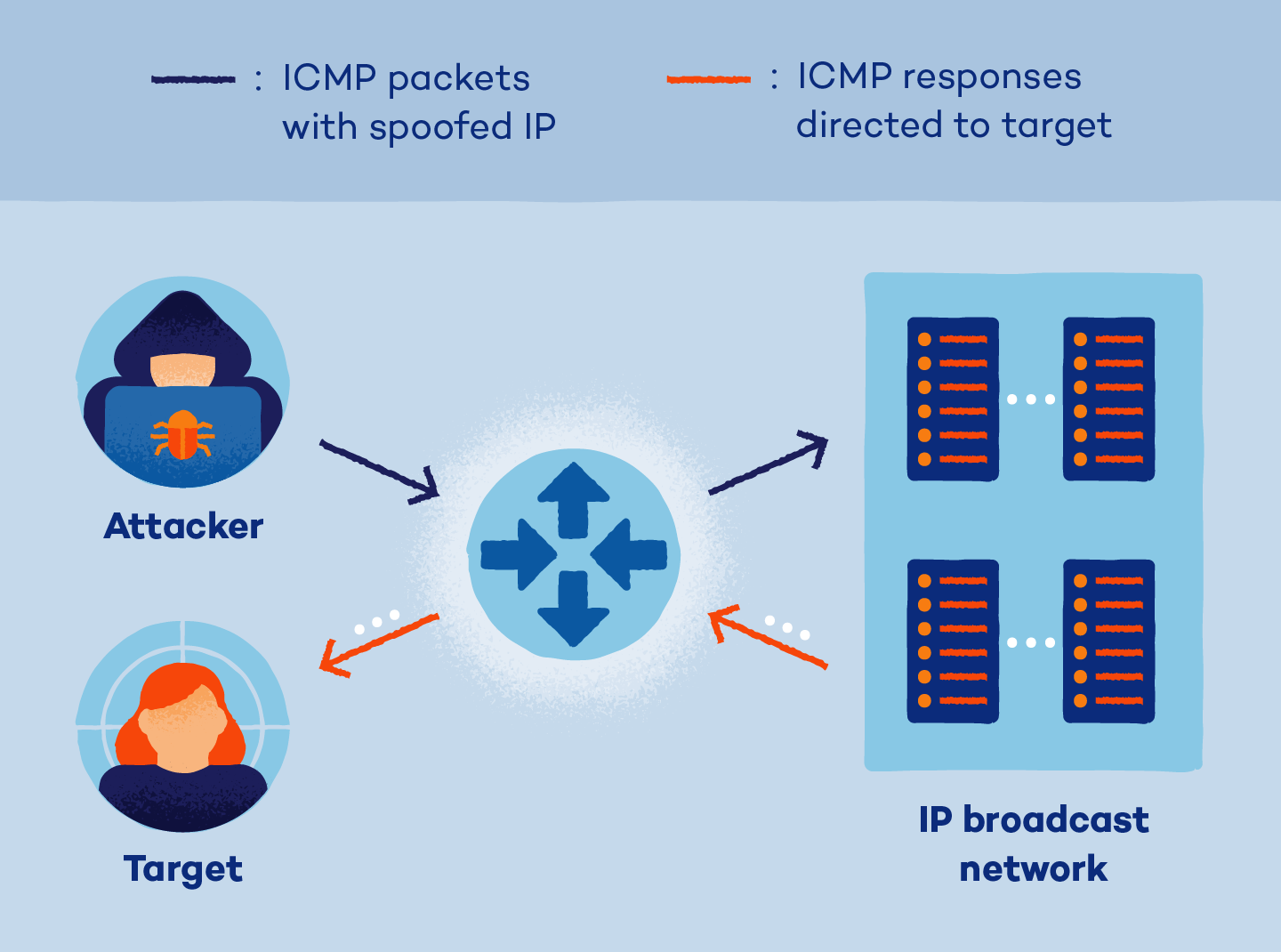
And because they are difficult to detect, smurf attack prevention techniques are crucial for avoiding them. Copywriter the smurf attack is an unusual threat in the wide realm of cybersecurity. This is known as spoofing.
A denial of service attack’s intent is to deny legitimate users access to a resource such as a network, server etc. Make sure to block directed broadcast traffic coming into the network configure hosts and routers not to respond to. This process, known as icmp echoes, creates an infinite.
Ask question asked 8 years, 8 months ago modified 8 years, 7 months ago viewed 7k times 7 i am using college network to access. There are two types of attacks, denial of. Definition & defense learn how adaptive multi.
A smurf amplifier is a computer network that lends itself to being used in a smurf attack. Protecting against smurf attacks. Faqs why is it called a smurf attack?